Use this Security Plan template to describe the system’s security requirements, controls, and roles / responsibilities of authorized individuals. This 25 page Word template and 7 Excel templates including a Threats Matrix, Risk Assessment Controls, Identification and Authentication Controls, Controls Status, Access Control Lists, Contingency Planning Controls, and an Application Inventory Form. Use this template to:
- Review security controls when system modifications are made.
- Eliminate security vulnerabilities related to systems configurations.
- Implement uniforms security controls across systems and databases.
- Identify penalties for different levels of security breaches.
MS Word Template: Blue Theme Screenshots
You can also specify who creates user accounts, conventions for usernames and passwords, access requirement and identify how users are tracked, sensitive information is managed and steps to take for data protection.
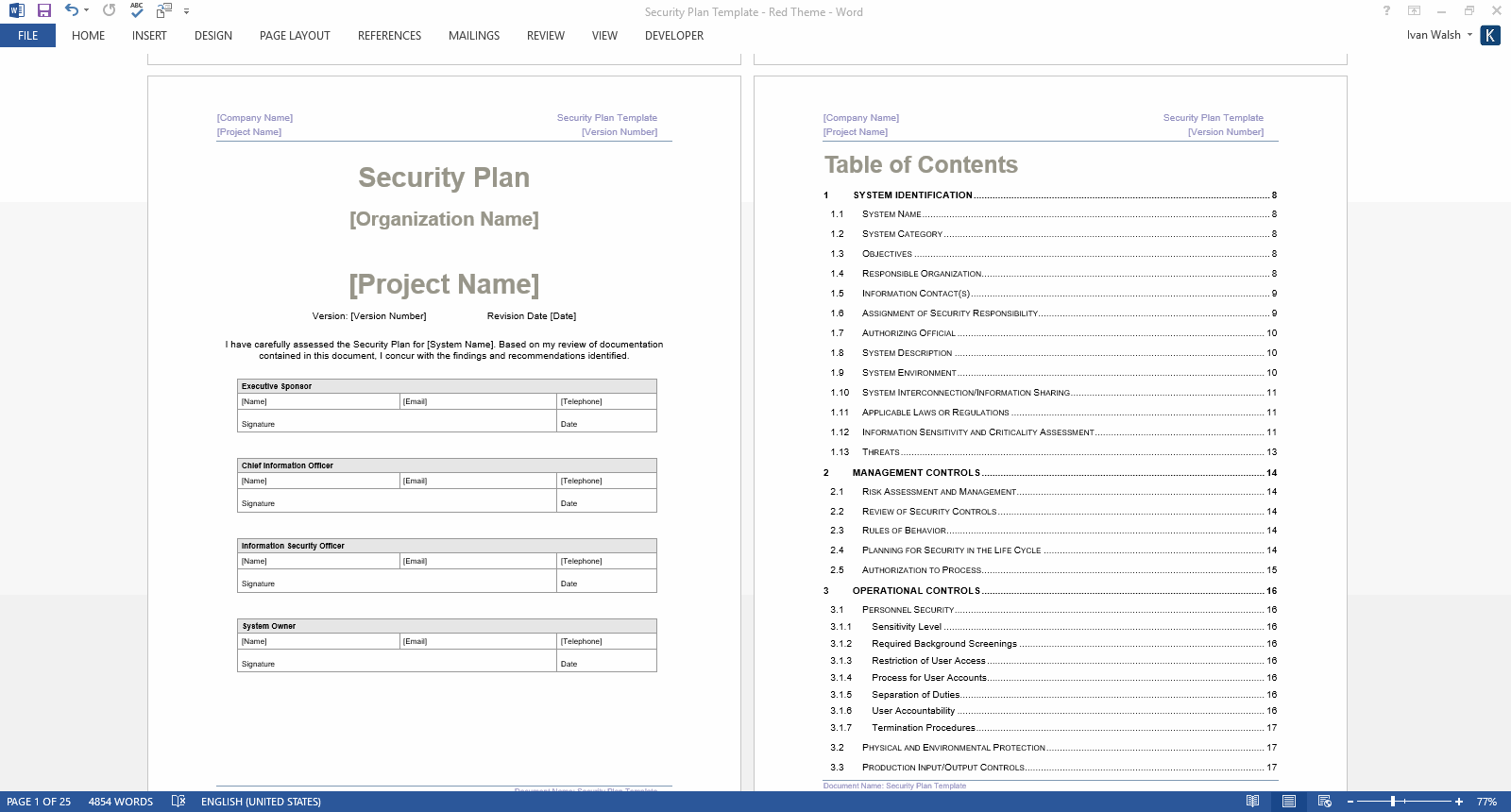
MS Word Template: Red Theme Screenshots
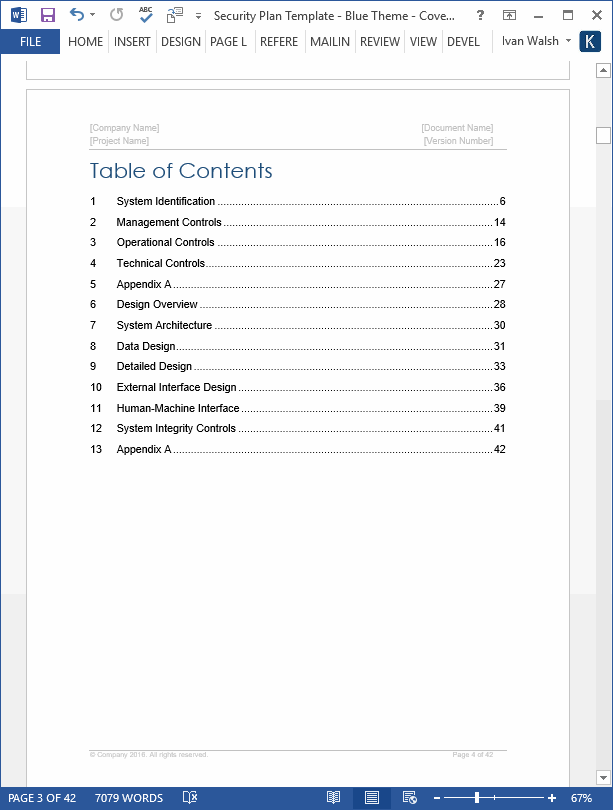
Table of Contents
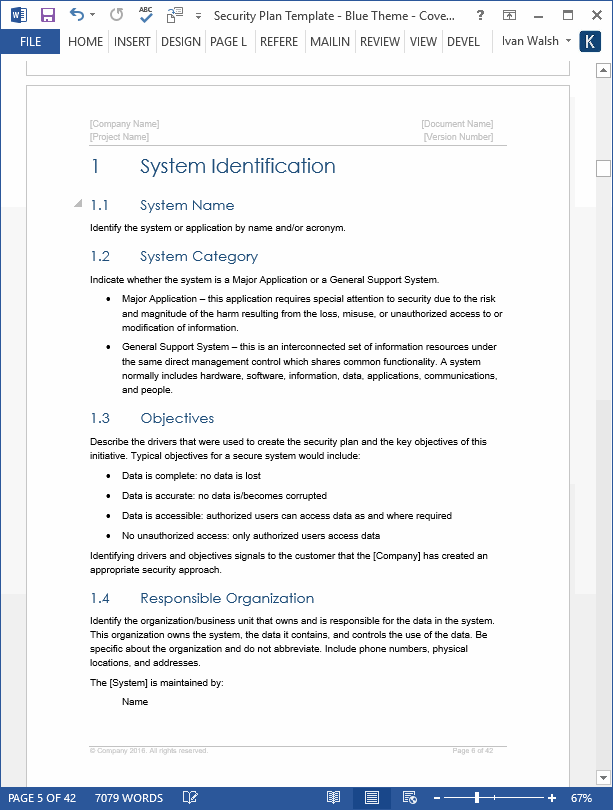
1 System Identification
1.1 System Name
1.2 System Category
1.3 Objectives
1.4 Responsible Organization
1.5 Information Contacts
1.6 Assignment of Security Responsibility
1.7 Authorizing Official
1.8 System Description
1.9 System Environment
1.10 System Interconnection/Information Sharing
1.11 Applicable Laws or Regulations
1.12 Information Sensitivity and Criticality Assessment
1.13 Threats
2 Management Controls
2.1 Risk Assessment and Management
2.2 Review of Security Controls
2.3 Rules of Behavior
2.4 Planning for Security in the Life Cycle
2.5 Authorization to Process
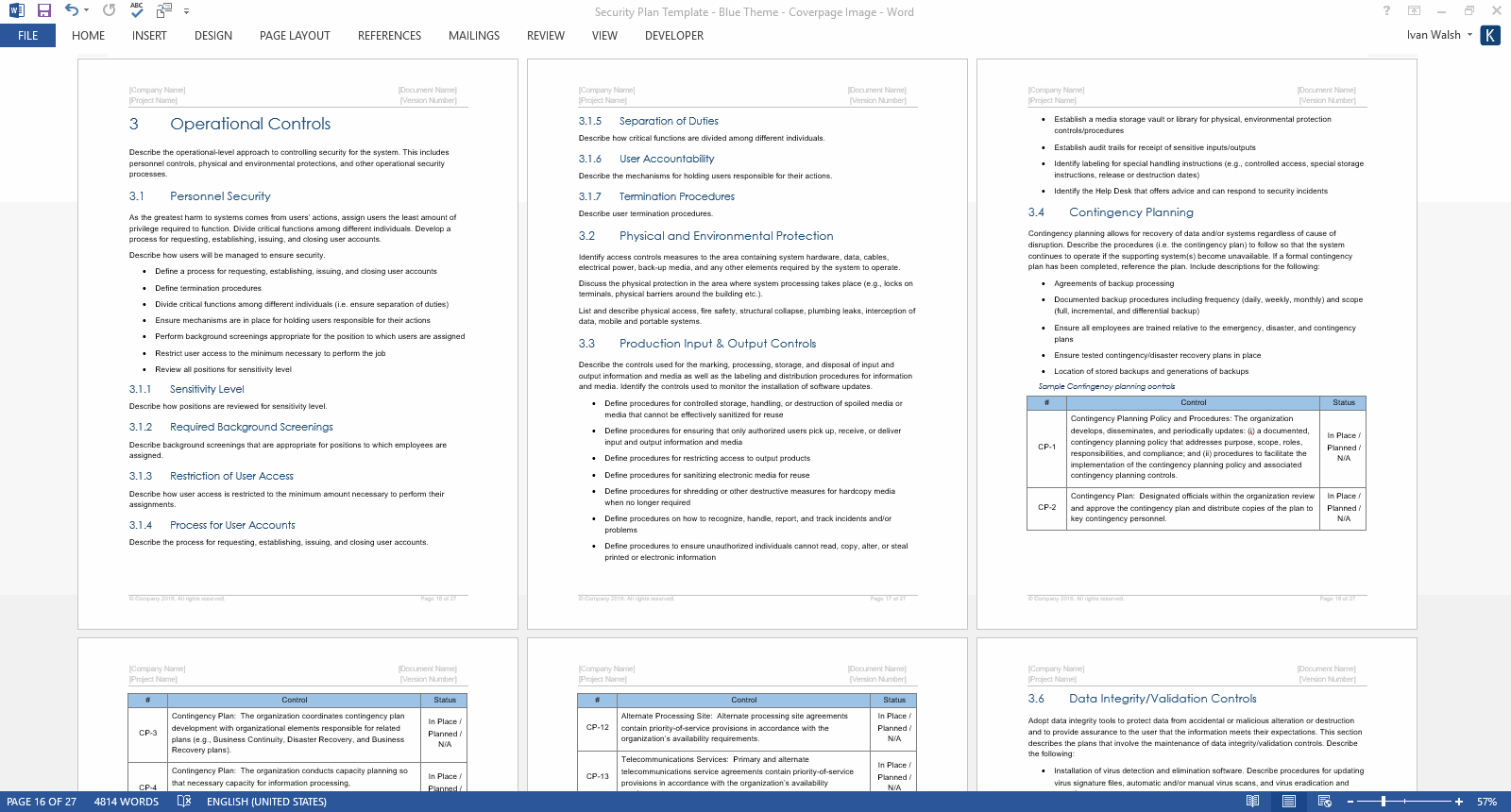
3 Operational Controls
3.1 Personnel Security
3.1.1 Sensitivity Level
3.1.2 Required Background Screenings
3.1.3 Restriction of User Access
3.1.4 Process for User Accounts
3.1.5 Separation of Duties
3.1.6 User Accountability
3.1.7 Termination Procedures
3.2 Physical and Environmental Protection
3.3 Production Input/Output Controls
3.4 Contingency Planning
3.5 Hardware and Software Maintenance Controls
3.6 Data Integrity/Validation Controls
3.7 Documentation
3.8 Security Awareness and Training
3.9 Incident Response Capability
4 Technical Controls
4.1 Identification and Authentication
4.1.1 Password Policy
4.1.2 Account Lockout Policy
4.1.3 Kerberos Policy
4.2 Logical Access Controls
4.3 Public Access Controls
4.4 Audit Trails
4.4.1 Audit Policy
4.5 Ongoing Security Management
5 Appendix A
5.1 Glossary of Terms
Contents & Format
The templates are in Microsoft Word and Excel format and can be downloaded online for only $9.99. The template pack includes the following documents:
| Security Plan | 25 pages x MS Word | |
| Application Inventory Form | 1 x MS Word form | |
| Threats Matrix | 1 worksheet | |
| Risk Assessment Controls | 1 worksheet | |
| Identification and Authentication Controls | 1 worksheet | |
| Controls Status | 1 worksheet | |
| Access Control Lists | 1 worksheet | |
| Contingency Planning Controls | 1 worksheet |